CONFIGURE HTTP/HTTPS SERVER ON CISCO ROUTER
DESCRIPTION
In this tutorial, we are going to learn many concepts of networking and security.
Networking
[+] We create a design of the network.
[+] We configure the network which consist of:
Configure hostname, domain name.
Generate crypto keys
Configure line vty, interfaces, DHCP Pool.
Create the user.
Configure the HTTP and HTTPS on cisco router.
[+] We verify the accounts by accessing through telnet and SSH.
[+] Access cisco router through browser. (Last activity).
Security
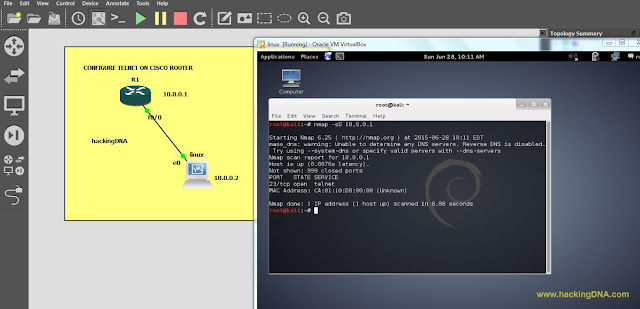
[+] In security, we perform network mapping using nmap tool.
[+] Check how many ports are open after configuring the services on cisco router.
[+] Check version of services running on port 80,443.
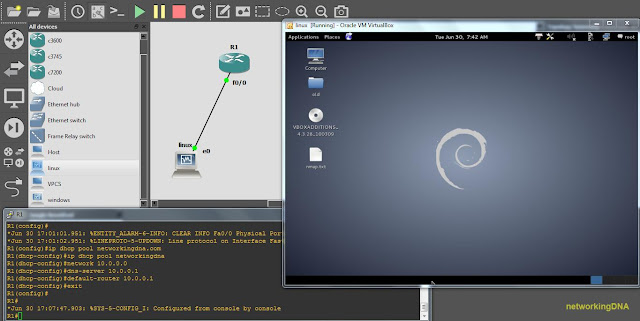
NETWORK SCENARIO
[+] Again in this tutorial, we take a very simple network scenario which consists of one cisco router 7200 series and one virtual machine ( running kali linux).
[+] See the below image for more details about the network.
CONFIGURE HTTP AND HTTPS SERVER
CONFIGURE HOSTNAME
R1(config)#hostname router1
CONFIGURE DOMAIN NAME
router1(config)#ip domain-name hackingdna.com
GENERATE CRYPTO KEYS
router1(config)#crypto key generate rsa general-keys modulus 1024
PERFORMING ENUMERATION OF HTTP AND HTTPS
VERSION SCAN
ACCESSING ROUTER PAGE THROUGH HTTPS
ENTER THE USERNAME PASSWORD
FINALLY YOU REACHED YOUR DESTINATION
AT THE END
DESCRIPTION
In this tutorial, we are going to learn many concepts of networking and security.
Networking
[+] We create a design of the network.
[+] We configure the network which consist of:
Configure hostname, domain name.
Generate crypto keys
Configure line vty, interfaces, DHCP Pool.
Create the user.
Configure the HTTP and HTTPS on cisco router.
[+] We verify the accounts by accessing through telnet and SSH.
[+] Access cisco router through browser. (Last activity).
Security
[+] In security, we perform network mapping using nmap tool.
[+] Check how many ports are open after configuring the services on cisco router.
[+] Check version of services running on port 80,443.
NETWORK SCENARIO
[+] Again in this tutorial, we take a very simple network scenario which consists of one cisco router 7200 series and one virtual machine ( running kali linux).
- Network: 10.0.0.0
- Router IP: 10.0.0.1
- Linux IP: 10.0.0.2
[+] See the below image for more details about the network.
CONFIGURE HOSTNAME
R1(config)#hostname router1
CONFIGURE DOMAIN NAME
router1(config)#ip domain-name hackingdna.com
GENERATE CRYPTO KEYS
router1(config)#crypto key generate rsa general-keys modulus 1024
CONFIGURE LINE VTY
router1#config t
router1(config)#line vty 0 4
router1(config-line)#login local
router1(config-line)#end
router1#
CONFIGURE INTERFACE
router1#config t
router1(config)#int f0/0
router1(config-if)#ip add 10.0.0.1 255.0.0.0
router1(config-if)#no shut
router1(config-if)#exit
router1(config)#
CONFIGURE DHCP POOL
router1(config)#ip dhcp pool networkingdna
router1(dhcp-config)#network 10.0.0.0
router1(dhcp-config)#dns-server 10.0.0.1
router1(dhcp-config)#default-router 10.0.0.1
router1(dhcp-config)#exit
router1(config)#end
router1#
CONFIGURE HTTP SERVER
router1(config)#ip http server
router1(config)#ip http secure-server
router1(config)#ip http authentication local
CREATE USER
router1(config)#username vivek privilege 15 password 0 12345
router1(config)#logging buffered 51200 warning
router1(config)#
VERIFYING SSH
ACCESS TELNET
PERFORMING ENUMERATION OF HTTP AND HTTPS
VERSION SCAN
- Find out what information you will get when you perform a version scan on port 80 and 443
- See the below output of nmap:
SSLSCAN
- Now we know that ssl is running on port 443. Lets confirm it which version of ssl is running on this cisco router.
- We can make this work easier by using sslscan. You can find this tool easily on kali linux or simply you can download from the repositories.
- Lets see the output of sslscan.
ACCESSING ROUTER PAGE THROUGH HTTPS
- To access this page, open your web browser and enter the router ip address.
- As you enter the router ip, it shows some exception. Click on add exception to move forward.
- See the below image for more help-
- To access the router, we need to enter the (username) and password (12345).
- See the below image for more details:
FINALLY YOU REACHED YOUR DESTINATION
AT THE END
- If you configure and practice this way you can make your networking and security more interesting.
- I hope this tutorial help all many of you.
- If you like this post you can share with your friends or comment here.
- Keep following us for more interesting tutorials.
- You can also join us on our facebook pages. Links are below
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSES ONLY/-